Encrypting all audio, video and data communications exchanged during a videoconference is possible with Tixeo’s end-to-end encryption technology. But how does it work?
Why use end-to-end encryption?
During videoconference meetings, a lot of personal and confidential information is exchanged. Without protection, this data is vulnerable to interception and eavesdropping. This risk of intrusion has particularly serious consequences for companies, which may be exposed to data theft and industrial espionage.
Reliable technology for confidential exchanges
End-to-end encryption (E2EE) is a system for transmitting data (audio, video and data). It allows only the sender and the recipient(s) to decrypt this data without any decryption phase between them. Eavesdropping and computer espionage are impossible. It is the only process that guarantees total confidentiality of communications.
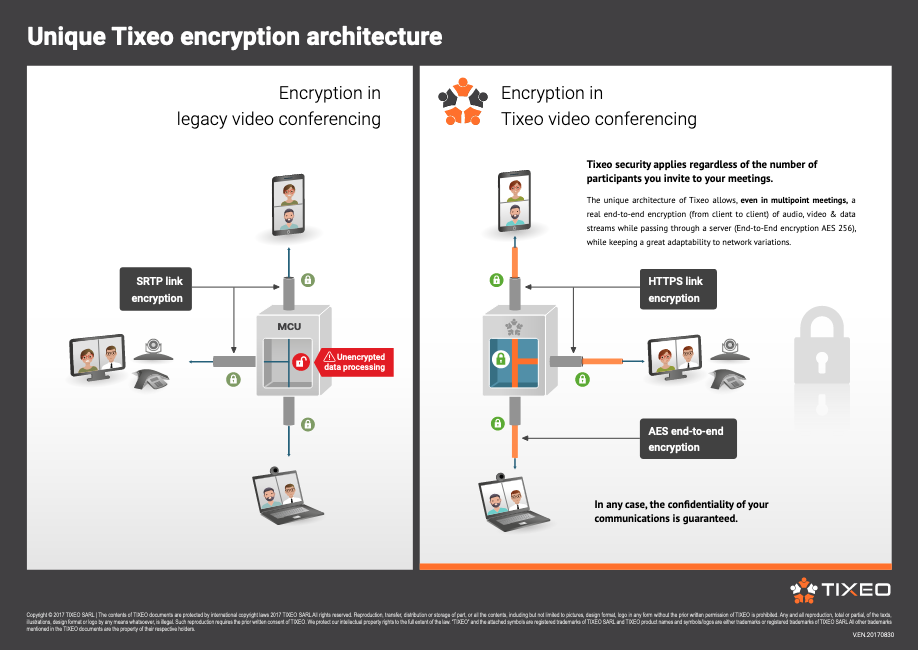
Tixeo video conferencing technology integrates true end-to-end encryption in a video conference, regardless of the number of connected users. Only meeting participants, who have the encryption keys, are able to access the exchanges. Tixeo, the editor, cannot intercept the communications either.
Tixeo’s unique end-to-end encryption architecture
Link encryption is done in TLS (Transport Layer Security). End-to-end encryption (client to client) of audio, video, and data streams is done in AES 256 (Advanced Encryption Standard 256), with a Diffie-Hellman key exchange. All data transmissions via Tixeo solutions are thus guaranteed to be at an optimal security level.
The key exchange “Diffie Hellman”
This is the mechanism chosen by Tixeo, used for end-to-end encryption key exchange. When a user logs in to his Tixeo account, a short-lived encryption key is assigned to him and stored on his device. It allows to encrypt all his audio, video and data communications.
To exchange with another user, the encryption key is communicated to the other user, and vice versa. If other users tried to access their communications, they would only see a string of unreadable numbers. The next time the user logs on to the software, a new encryption key is assigned.
No trace of the communications can be found thanks to this procedure.
The true or false of end-to-end encryption
Do all video conferences encrypt their communications?
False !
Some traditional video conferences claim to have end-to-end encryption of communications. In most cases, this is simple SRTP (Secure Real-time Transport Protocol) link encryption. In fact, this technology encrypts only the flows between the user and the communication server. It is therefore very easy to access the decrypted data when it passes through their servers. With Tixeo’s secure technology, the server relays an encrypted version of the exchanges that no one is able to decrypt if they don’t have the key.
Some traditional video conferencing systems are based on SIP or H.323 protocols. Because of this architecture, these systems cannot natively integrate end-to-end encryption mechanisms.
Tixeo is Secure by design
Tixeo video conferencing technology is Secure by design. Tixeo initially designed its architecture to allow true end-to-end encryption of communications, even in multi-point video conferencing. This architecture is based on the SVC on Demand (Scalable Video Coding on Demand) technology developed by Tixeo teams. This technology takes into account network quality, CPU performance and the size of the participants’ windows in order to offer the highest stability to communications.
Is end-to-end encryption not possible in some countries?
TRUE !
Outside Europe, data protection guarantees are limited. End-to-end encryption of communications is sometimes non-existent or prohibited.
For more than 20 years, the USA PATRIOT Act has potentially authorised the tapping of any type of electronic communication. Thus, US government agencies require national IT companies operating in the United States or elsewhere to provide (if necessary) means of data collection or “backdoors”. The risk of espionage is therefore high if one considers that these backdoors are likely to be used by malicious entities. Moreover, such eavesdropping is not limited to the United States. Companies in other countries are constrained by equivalent regulations.
The origin of an encryption technology therefore remains a crucial element to take into account when choosing a videoconferencing solution. In Europe, thanks to GDPR, no text prohibits end-to-end encryption, and no law can force a publisher to provide encryption keys. This legal framework is of paramount importance: it guarantees optimal protection against any attempt to eavesdrop.