End-to-end encryption
The only technology
for true communication privacy
Tixeo protects your online meetings with genuine end-to-end encryption.
One key is all it takes to meet and share securely
End-to-end encryption is a highly secure system for transmitting communications. This technology prevents any interception of data, including by the service providers themselves.
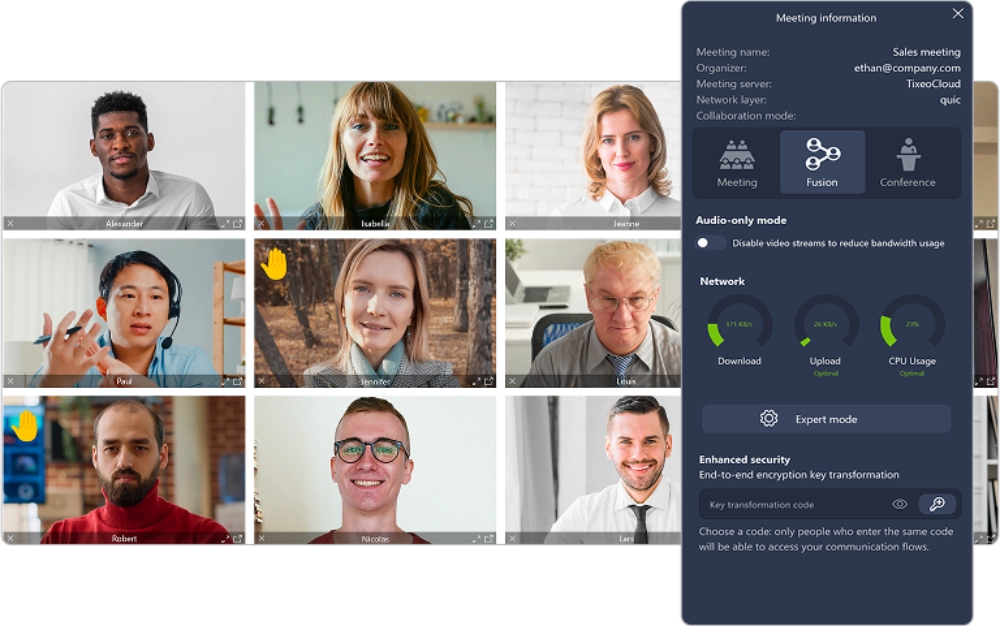
At the core of Tixeo’s secure video conferencing
Protect your sensitive communications from espionage
Certain types of sensitive, confidential, or personal information must never be exposed.
Tixeo’s technology guarantees that video, audio and data streams (files and messages exchanged) remain inaccessible to third parties, regardless of the number of videoconference participants.
 |
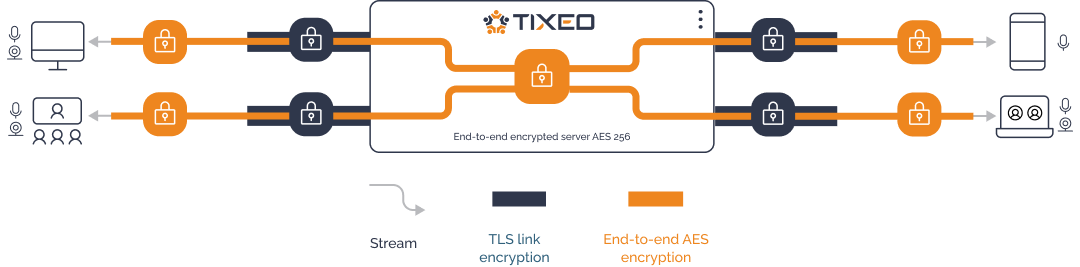
Security is taken into account at every stage of Tixeo's design using the Security by design approach. Its End-to-End Encryption (E2EE) technology is activated by default. |
 |
AES 256 encryption is used to secure data transmission; the server relays encrypted content without access to decryption keys. This mechanism prevents any attempt at a man-in-the-middle attack, and is highly adaptable to network variations. Communication flows remain encrypted, even at the level of the server. |
 |
The link is encrypted using TLS (Transport Layer Security) to ensure data protection. |

Secure by Design
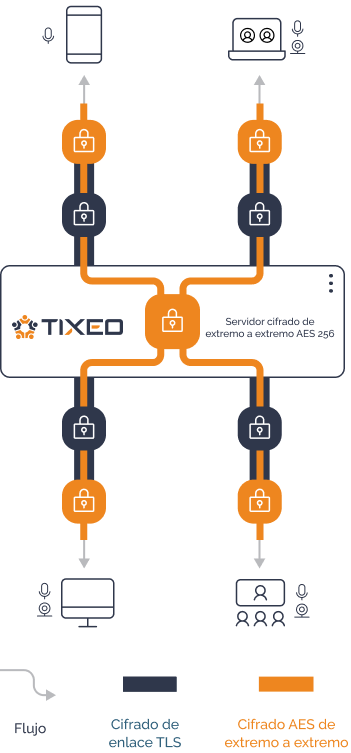
Security is taken into account at every stage of Tixeo’s design using the Secure by design approach. Its End-to-End Encryption (E2EE) technology is activated by default.

AES 256 encryption is used to secure data transmission; the server relays encrypted content without access to decryption keys.
This mechanism prevents any attempt at a man-in-the-middle attack, and is highly adaptable to network variations. Communication flows remain encrypted, even at the level of the server.

TLS (Transport Layer Security) link encryption
The link is encrypted using TLS (Transport Layer Security) to ensure data protection.
End-to-end encryption: myth vs reality
“All video conferencing solutions offer end-to-end encryption.”
“All video conferencing solutions offer end-to-end encryption.”
 False
False
Traditional video conferencing often uses SRTP link encryption. This type of encryption does not secure communications that pass through the server and exposes you to cyber espionage and the risk of data loss.
Other applications offer only Point-to-Point Encryption (P2P), limited to two participants, or offer end-to-end encryption only for their messaging.
“Most video conferencing applications have backdoors.”
“Most video conferencing applications have backdoors.”
 True
True
In some countries, such as the United States, legislation requires publishers of video conferencing solutions to give the authorities access to communications passing through their platform via backdoors. These backdoors constitute security loopholes, since a malicious person or group of cyber-attackers can use them to access data.
European video conferencing solutions, such as Tixeo, are not subject to this obligation.
Benefits of Tixeo end-to-end encryption

Communications security
No one outside a Tixeo video conference can access communications thanks to end-to-end encryption by default. Files exchanged in instant messaging are never stored on the server.

Guaranteed sovereignty
Rely on European end-to-end encryption technology, designed in France, with no backdoors, to limit the risks of eavesdropping and foreign interference.
Guaranteed sovereignty
Rely on European end-to-end encryption technology, designed in France, with no backdoors, to limit the risks of eavesdropping and foreign interference.

Protection of classified information
Tixeo’s Enhanced Security mode significantly enhances end-to-end encryption performance and preserves the secrecy of classified or restricted documents.
Protection of classified information
Tixeo’s Enhanced Security mode significantly enhances end-to-end encryption performance and preserves the secrecy of classified or restricted documents.

Tixeo, a European solution, is compliant with the General Data Protection Regulation (GDPR) and is not subject to any extra-territorial laws.

Since 2017, the French Cybersecurity Agency (ANSSI) has renewed Tixeo’s CSPN certification three times, proof of its reliability and commitment to cybersecurity.
How does it work?
Also known as Diffie-Hellman key exchange, this end-to-end encryption system generates a different encryption key for each connection. No trace of communications can be found.
Also known as Diffie-Hellman key exchange, this end-to-end encryption system generates a different encryption key for each connection. No trace of communications can be found.


You connect to Tixeo to join a meeting.
You are assigned a unique, temporary encryption key.


You securely join your online meeting
Your encryption key is transmitted automatically to your contacts, and you receive theirs, so you can communicate in complete confidentiality.
All communications (audio, video and file sharing) are encrypted, and can only be decrypted using your encryption key.


If other people try to access your communications,
All they would see is a series of unreadable numbers because they don’t have your key.
The next time you connect to the software, you will be assigned a new encryption key.
Boost your security on demand
With Tixeo, take control of your encryption key thanks to a new feature: Augmented Security.
During an encrypted video conference with several participants, you need to increase your security or exchange sensitive information with some of the participants, for example :
- Authentication data,
- Classified documents,
- Specific internal procedures,
- or any other critical subject.
Enter a secret, ephemeral communication tunnel.
Secret and temporary communication tunnel
1 Secret code
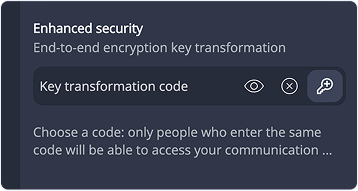
During a secure conversation, define a secret code to be entered into the application by each of the participants in the exchange. This code temporarily transforms the initial encryption key to access a dedicated communication tunnel.
2 Dedicated communication tunnel

Only participants who have entered the same code are in this tunnel. All communication flows (audio, video and data) are then invisible to any other person who has not entered the code in the meeting.
3 Back to the initial meeting
To return to the original encrypted meeting, everyone deletes the code entered in the application. Your original encryption key is restored.
This innovative Key Derivation Function meets the needs of the most demanding users in terms of cyber security.
Benefits of Tixeo Augmented Security
- Reinforce user control in the communication process, using a secret code to be defined preferably by telephone or text message
- Avoid the risks of identity theft and deep fake in video conferencing
- Protecting highly critical exchanges

Amid escalating cyberwarfare,
securing communications is critical

“According to the ENISA (European Union Agency for Cybersecurity) report published in September 2024, espionage is among the top 5 cyber threats to organisations today.”


 Renaud Ghia,
Renaud Ghia,
Chairman of Tixeo
“With backdoors installed in video conferencing software, organisations no longer have any guarantee of protection for their sensitive exchanges. End-to-end encryption is the only technology capable of offering the highest level of confidentiality for secret communications.
In February 2024, the Court of Justice of the European Union ruled that any action to weaken encryption would be contrary to European law.”

Over the past 20 years, Tixeo has become a key player in France’s cybersecurity and secure communications ecosystem. Its end-to-end encryption technology is fully developed in-house by its R&D teams, ensuring complete technological independence.

Over the past 20 years, Tixeo has become a key player in France’s cybersecurity and secure communications ecosystem. Its end-to-end encryption technology is fully developed in-house by its R&D teams, ensuring complete technological independence.
Everything you need to know about end-to-end encryption
for video conferencing
Definition and operation of end-to-end encryption
What is the definition of end-to-end encryption?
End-to-end encryption, or E2EE encryption, guarantees that only the senders and receivers of communications can encrypt and decrypt the data exchanged. This process of securing information relies in particular on the use of message encryption and decryption keys.
What's the difference between encryption and cryptography?
Encryption transforms data into an unreadable format using a key to protect it from unauthorised access. Cryptography is a broader field that encompasses all techniques and principles used to secure data and communications, including encryption, digital signatures, authentication, and security protocols.
How does end-to-end encryption work?
End-to-end encryption works according to the protocol used by the video conferencing provider. This may involve symmetric or asymmetric encryption, encryption in transit and at rest, or public/private key systems.
Tixeo uses the Diffie-Hellman key exchange: each time a user connects, a temporary encryption key is generated and stored locally to secure all communication flows. This key is then shared with authorised participants. Anyone without the key sees only unreadable data. A new key is generated on each new connection.
Importance and benefits of end-to-end encryption
Why is this technology essential for communications?
Geopolitical tensions and cyberwarfare are increasing the risk of critical communications being compromised. For organisations in sensitive sectors, securing exchanges has become essential. The European NIS 2 Directive even recommends the use of end-to-end encrypted communications.
What are the advantages of Tixeo end-to-end encryption?
End-to-end encryption guarantees the confidentiality and protection of exchanged data. This protocol secures your communications and protects sensitive information from intrusion.
- Confidentiality: Prevents interception by any third party, including service providers.
- Advanced technology: Uses AES-256 for encryption and TLS for securing data in transit.
- Secure messaging: All video and message communications are encrypted, regardless of participant count.
- Sovereignty and compliance: Developed in France, GDPR-compliant, and free of backdoors.
- Enhanced protection: With Augmented Security, users can create an isolated communication tunnel for ultra-sensitive exchanges.
How does end-to-end encryption protect data and privacy?
End-to-end encryption protects data by encrypting it before it leaves the user's device. This process prevents any malicious interception during transmission and until the secret, ephemeral key stored in the recipient's device is able to decrypt the message.
This technology offers the highest level of privacy protection. In Europe, no authority (internal or external) can legally gain general access to end-to-end encrypted discussions. Targeted access is only possible as part of a judicial investigation, with strict guarantees and without weakening the security of all users.
Applications and threats to end-to-end encryption
Which applications use end-to-end encryption?
Many encrypted instant messaging applications use end-to-end encryption, including WhatsApp, Microsoft Teams, Zoom, Signal, Google messages and Telegram. But some video conferencing platforms offer it partially or for specific features only, and may be subject to foreign regulations requiring backdoors. This undermines the protection offered by encryption.
How do I activate end-to-end encryption?
Activating end-to-end encryption varies depending on the applications and email services. Generally, this requires specific configuration in the security settings of the application used and can generate compatibility problems. With Tixeo, no settings are required: end-to-end encryption is enabled by default in online meetings, regardless of the number of participants.
What are backdoors in a communications solution?
A backdoor provides secret access to exchanged data and communications. It is known only to the publisher and the authorities for whom it is usually created. But if a malicious person or group of hackers assumes its existence, they can easily find it and use this access to spy on exchanges. A backdoor is therefore a potential security risk for video conferencing.
Why is end-to-end encryption under threat?
More and more legislators are attacking end-to-end encryption algorithms, accusing this type of technology of hampering the fight against crime and terrorism. Weakening end-to-end encryption and imposing back doors in communication platforms represents a danger to the protection of sensitive information in many critical organisations. Criminals will always get round the lack of encryption in an application by using another encrypted communication channel.
